If you’re reading this post, you are probably more or less familiar with brand new AMP for Emails technology developed by Google. It turned out that new horizons are opened wide for the commercial email channel. Therefore email marketers don’t have to retrain into plumbers or waiters. However, new skills and knowledge are obviously required to obtain. But that’s a matter for a separate talk.
Today we’re going to pay attention to new specific issues of internet security that accompany AMP innovations. In particular, to whitelisting – what is this about, why so secure and how to pass this “scary” challenge. Let’s get down to it.
AMP in a digital nutshell
Not going too deep into technical details, AMP (Accelerated Mobile Pages) is a new advanced technology of high-speed data transfer based on AMP HTML. In fact, these protocols are the next stage of classic HTML code evolution. But the complex of HTML upgrades gave birth to a new framework that allows applying and using various next-gen features that bring the whole Internet to a new level.
AMP implementation requires a deep redesign of the whole global network, that’s why this process is long-run. AMP for Emails is a new milestone in this way. It means that AMP-powered techniques are in the email communication channel now, and they brought us new opportunities to use advanced interactivity and dynamic real-time content.
The very beginning of AMP 4 Emails was so successful that it became the hottest trend 2019 in email marketing. AMP support is implemented by top email clients like Outlook and Yahoo as well as ESPs and template editors like eSputnik and Stripo.email.
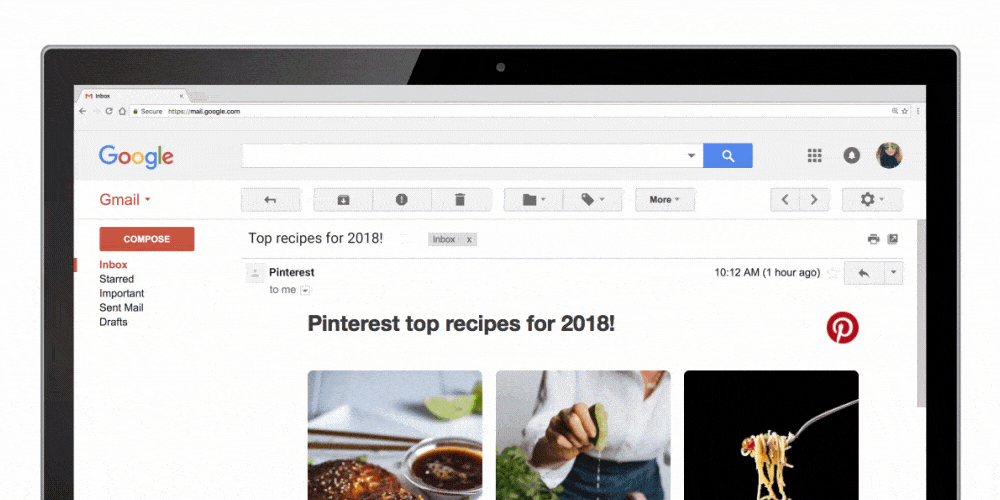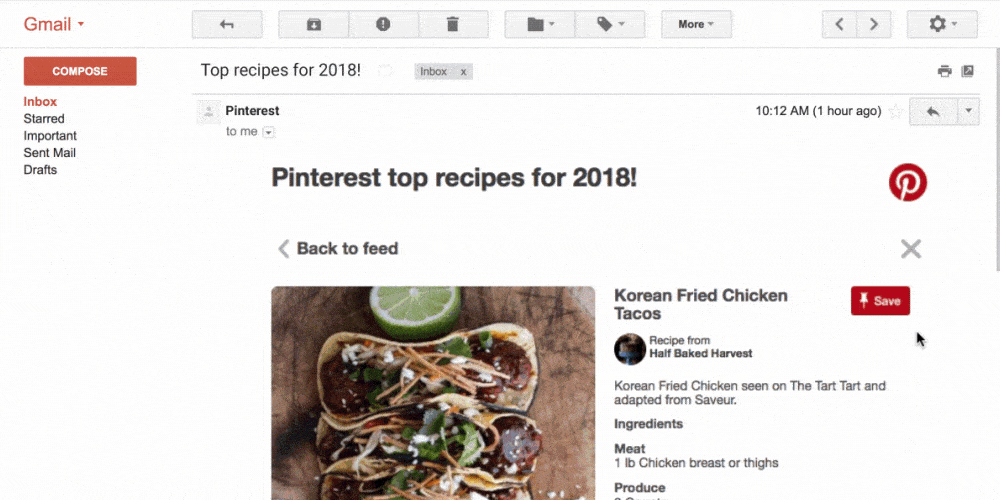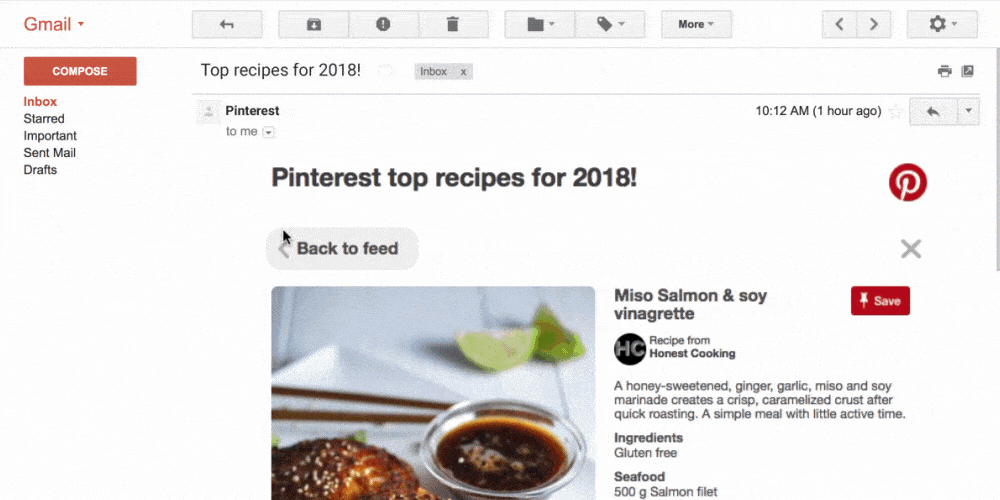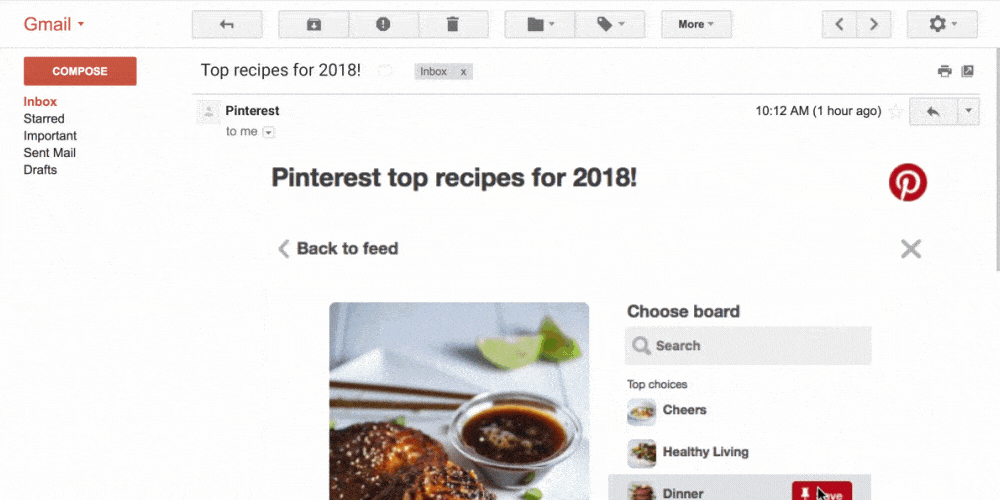
From now on, email is not an outdated digital letter anymore but a mini website right in the inbox folder. We send an email campaign – and our subscribers can preview all available product versions including zoom and snippets from different angles, check how many items are available right now, add goods to the cart, calculate the total amount and make an order.
Moreover, users can vote, leave comments and rate goods/services, talk in chats, order tickets and hotel rooms, track exchange rates and sports game score, confirm the meeting, etc. I repeat, all that is done right in inbox email in real-time mode. No need to navigate somewhere – yeah, clients are a bit lazy today… an effect of progress.
In addition, accordion menus and image carousels are much more convenient and stylish ways to show pics or arrange menus. All that looks amazing, no arguments. But…
There are two sides to each coin
…probably even to bitcoin 🙂 Besides jokes, it’s a principle of this world – nothing is 100% great and awesome. With AMP, new cyber threats arise.
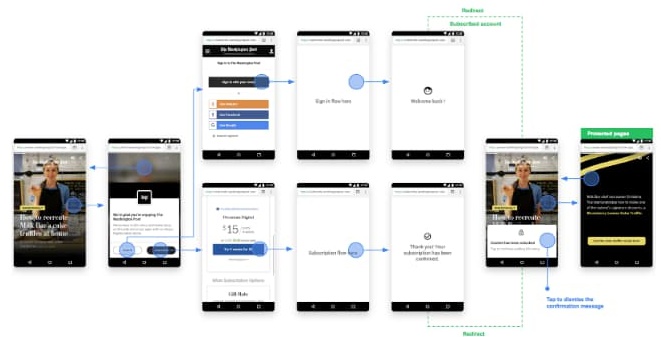
How does dynamic data transfer work? Let’s figure out the essential technical details. Shortly, dynamic content itself is not embedded in the email body. Only AMP-powered blocks are built in the message. They have permission to connect to constantly changing data stored on servers. Having access to the end-points, AMP blocks transfer input and output data displaying updated content in the client’s email. Then, AMP blocks transmit all their actions to company resources in turn. In other words, it’s a long sequence of mutual interaction: user’s device – email page – external resources, instead of “device/email”.
In these details, the Devil lurks.
Why so secure
I’ve met a post where the author said that AMP is such an evil that it’s better to deny it at all and disable all those options on our devices. This approach seems too pessimistic… following such logic, let’s shut down the Internet at all. No internet – no hackers, yeah ))) Absurd? Surely.
If there’s a backdoor in our house, should we brick it because our city is full of crimes? I guess no. But our task is to protect all doors and windows with proper security systems. The same goes for web security as a global network is Sin City too, not even mention the twilight zone called Darknet.
In fact, AMP-powered methods of data input/output are a real backdoor for bad guys of all sorts. You received an inbox message that includes elements with data exchange permission activated by default. This access needs no user’s actions to enable, otherwise, it would be inappropriately inconvenient. It sounds pretty frightening. Especially taking into account that AMP is about confidential data transfer.
Most of you are probably familiar with phishing emails. All those fake messages “from banks/social media admins/payment systems/Apple company etc” (in fact not from them). Imitation of corporate design, scary notifications “your account/card is blocked/suspended…” – and request to click the link and confirm personal data (by inserting it, of course). Such emails are typically removed immediately, accompanied offline with “warmest” wishes to the sender. Btw, we recommend to send reports to respective email services – it helps to stop those “wags”.
But… among thousand of experienced people, there is always one naive person who shares secret data – and in this case, phisher wins. Otherways they’d stop attempts long ago if they were futile.
Notice that the phishing method I explained above is quite primitive. Now imagine what hackers can do using AMP blocks. It may become a huge security breach opening ways for cybercrime, and not only rough phishing. Data transfer blocks may turn into infiltrator units to hack PCs and local networks, steal confidential and private data, disable software and hardware… On all scales, up to corporate espionage, state crimes, and cyber-terrorism.
How to prevent all that? Anti-malware techniques are different. But one of the key security tactics is exactly what is mentioned in the current post name.
Whitelisting by Google
You wondered why we need to get whitelisted by Google? I hope the answer is clear now: to avoid cyber attacks and data stealing. Google needs to ensure that you’re a trustworthy company or person, not a malicious intruder with intents to cheat and hack. Don’t be scared – as a rule, this sender verification is easy enough to pass successfully.
How to get whitelisted? First of all, craft your first AMP-powered campaign and choose proper ESP that supports bulk mailings with AMP elements in emails. Then, whitelisting is done this way:
- authenticate your sender name, settings of SPF and DKIM parameters, and check your XHRs destination;
- verify the white history of your mass mailings, domain reputation, and spam complaints rate – it must be low;
- send your first AMP message to Google;
- and fill out all fields in the Sender Registration form.
When all that is done, just wait. It takes time as whitelisting is not an automatic operation. Artificial intellect is still not smart enough to do this, so decisions are made not by machines. Human touch is required.
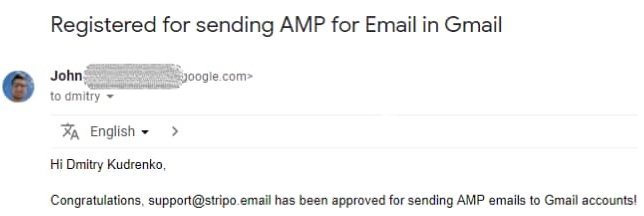
But when you’re finally whitelisted, there are no limits to send AMP-powered campaigns. Congratulations!
Summing up
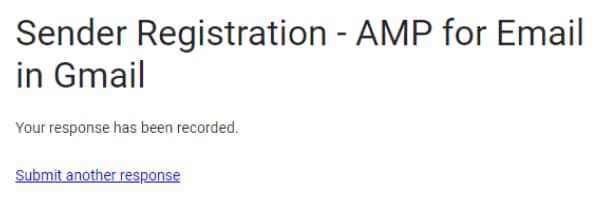
Notice that once you submit the Google registration form, you will see this notification:
And then a period of silence – no more notifications from Google team until the very day you get whitelisted. Don’t panic, everything is OK – your request is processed. As for our case, we waited for two weeks for the response.
We sincerely wish you to get whitelisted successfully – AMP emails are the new age of email marketing. And one more recommendation: time is money, so better spend the period of waiting for self-education on how to create the best AMP emails. As we said above, new skills are essential here.
Good luck!