Today, we published our research about Windows exploitation in 2014. This report contains interesting information about vulnerabilities in Microsoft Windows and Office patched over the course of the year, drive-by download attacks and mitigation techniques.
Today, we published our research about Windows exploitation in 2014. This report contains interesting information about vulnerabilities in Microsoft Windows and Office patched over the course of the year, drive-by download attacks and mitigation techniques.
The report includes the following information.
- Vulnerabilities discovered and patched in Microsoft Windows and Office.
- Statistics about patched vulnerabilities and how they compare with 2013’s statistics.
- Detailed descriptions of actual exploitation vectors.
- Vulnerabilities that were exploited in the wild, including a specific table showing ASLR bypass vulnerabilities.
- Exploitation methods and mitigation techniques for Microsoft’s Internet Explorer web browser (IE).
Last year we saw many exploits that were used for drive-by download attacks. Such attacks are used for silently installing malware. Our report contains detailed information about the nature of drive-by download attacks and how Internet Explorer was improved by Microsoft so that such attacks were mitigated by default.
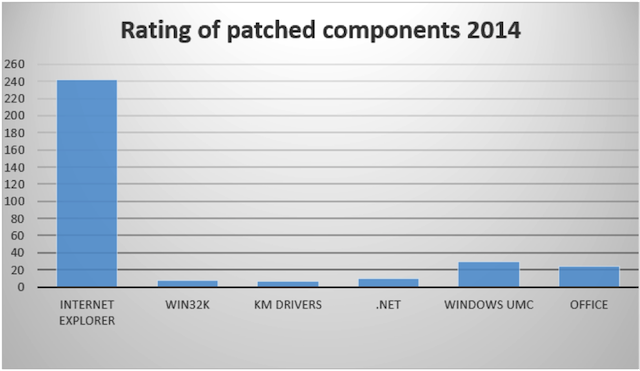
In the first figure below you can see that Microsoft fixed most of the vulnerabilities in Internet Explorer. Almost all of them belong to the Remote Code Execution type, that is, they can be used to implement drive-by download attacks. This figure includes information about vulnerabilities in Internet Explorer, the Windows GUI subsystem driver, kernel mode drivers, .NET Framework, Windows user mode components and Office.
Like we mention before an attacker could execute code remotely in a vulnerable environment, with the help of a specially-crafted web page. Such a web pages could contain special code, called an exploit, to trigger a specific vulnerability. Usually attackers use such exploits for silently installing malware when they detect a vulnerable Windows version. This attack is an example of a drive-by download and this is why we highlighted such exploitations as a major trend in attacks on Internet Explorer, as shown in the Figure below:
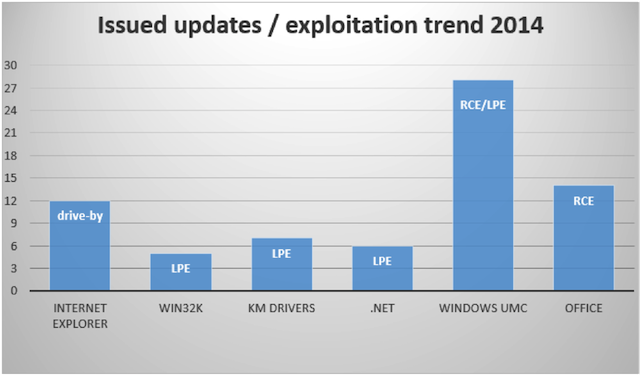
Our report includes a specific section describing mitigation techniques that were introduced by Microsoft in the last year. This section covers Windows, Internet Explorer and the EMET tool. Such security features address several types of attack surface. For example, a feature introduced for IE called Out-of-date ActiveX control blocking is useful for blocking all exploits based on vulnerabilities in old versions of Oracle’s Java plugin.
We also look at Local Privilege Escalation (LPE) attacks that are used by attackers for bypassing the browser’s sandbox or to run unauthorized code introduced by malware in kernel mode. In the last year Microsoft addressed a much smaller number of vulnerabilities for win32k.sys than it did in 2013. Unfortunately, today this driver is a major source of such vulnerabilities and often used by attackers.