Smart Sex Toys Can Be Switched On/Off and Exploited Remotely – Thanks To A Vulnerability.
Pen Test Partners (PTP) is a security group comprising of white hat hackers. Reportedly, PTP researchers have identified that it is quite easy to take control of Bluetooth butt plugs. This means, playing with your smart toys without even entering your house will be a piece of cake for cybercriminals.
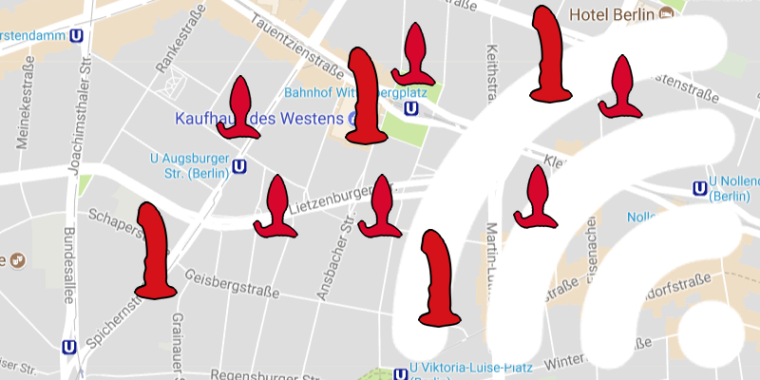
PTP showed how smart sex toys could be taken over, which refers to a practice called “screwdriving.” They proved how hackers could manipulate butt plug to make it go crazy and uncontrollable by detecting a smart sex toy known as Lovense Hush and set it on full power from outside its location.
‘One could drive the Hush’s motor to full speed, and as long as the attacker remains connected over BLE and not the victim, there is no way they can stop the vibrations… adult toys appeal to a huge spectrum of people, and their ubiquity allows people to enjoy a sex-positive life. However we think that these same people should be able to use them without fear of compromise or injury,’ wrote PTP researchers.
The reason why these toys could be manipulated from far away is that there is a vulnerability present in smart sex toys, especially those manufactured within the US. This flaw allows full control of the device from the street, as proven by Alex Lomas from PTP security group.
While wandering the streets of Berlin, Lomas discovered that suddenly an adult sex toy appeared on his smartphone. Naturally, Lomas was surprised and used the screwdriving technique to detect how hackers can locate a Bluetooth Low Energy, or BLE enabled smart sex toy accurately through triangulation.
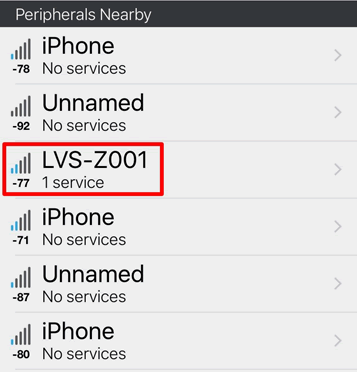
Connection received by Lomas
BLE is also called Bluetooth Smart. It is a wireless personal area network technology devised to make sure that the device consumes less power and runs on smaller battery for a longer duration than Bluetooth. BLE is commonly used in devices like health monitors, fitness trackers, mouse, and keyboards. If this technology is reliable enough to be used in smart devices from a security perspective is an aspect that has largely been ignored so far.
Lomas noted that BLE devices use the same identified across all devices and are thus, advertised as made for discovery. He identified that all Hush devices were dubbed as LVS-Z001.
Since Lovense Hush is BLE connected butt plug, therefore, it was easily detected by Lomas. This device allows users to control vibration speed through their smartphones fully and can be used by long-distance couples by using a mobile app and use options like Solo Play or Discreet Public Play with BLE.
Several other devices were also tested by researchers such as another US make sex toy Kiiroo Fleshlight and Lelo, Lovense Nora and Max. It was identified that none of these devices used a password or PIN to be accessed and if any did use one, it was static or generic. This issue was discovered in “every Bluetooth adult toy” that the researchers tested. Hence, researchers concluded that these Bluetooth sex toys don’t include UI (user interface) due to which it is possible to connect the toy to another device having pairing PIN.

Since the communication between the toy and phone is performed via BLE signals, which are not encrypted, therefore, researchers could intercept the transmissions between toy and phone using a single Bluetooth dongle and an antenna. Afterwards, Lomas demonstrated that using a few basic commands can let a hacker to create a connection with the device and control them from outside the house, from a street.
Moreover, BLE devices utilize P2P (point-to-point) topology to initiate one-on-one device communications, therefore, as long as the attacker is controlling the device the vibrations will continue, said Lomas.