Search results for "Windows"
-

 2.8KVulnerabilities
2.8KVulnerabilitiesRussia’s APT28 Exploited Windows Print Spooler Flaw to Deploy ‘GooseEgg’ Malware
The Russia-linked nation-state threat actor tracked as APT28 weaponized a security flaw in the Microsoft Windows Print Spooler component to deliver a...
-

 4.1KVulnerabilities
4.1KVulnerabilitiesResearchers Uncover Windows Flaws Granting Hackers Rootkit-Like Powers
New research has found that the DOS-to-NT path conversion process could be exploited by threat actors to achieve rootkit-like capabilities to conceal...
-

 4.3KVulnerabilities
4.3KVulnerabilitiesCritical ‘BatBadBut’ Rust Vulnerability Exposes Windows Systems to Attacks
A critical security flaw in the Rust standard library could be exploited to target Windows users and stage command injection attacks. The...
-

 4.9KMalware
4.9KMalwareDetecting Windows-based Malware Through Better Visibility
Despite a plethora of available security solutions, more and more organizations fall victim to Ransomware and other threats. These continued threats aren’t...
-
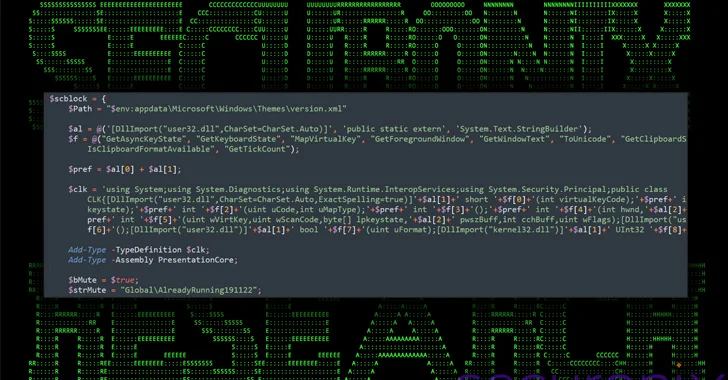
 2.8KMalware
2.8KMalwareNew DEEP#GOSU Malware Campaign Targets Windows Users with Advanced Tactics
A new elaborate attack campaign has been observed employing PowerShell and VBScript malware to infect Windows systems and harvest sensitive information. Cybersecurity...
-

 1.3KData Security
1.3KData SecurityCVE-2023-5528: Kubernetes Flaw Jeopardizing Windows Node That Can’t Be Ignored
In recent developments, cybersecurity experts have raised alarms over a high-severity vulnerability identified in Kubernetes, marked as CVE-2023-5528. This critical flaw has...
-

 1.9KVulnerabilities
1.9KVulnerabilitiesResearchers Detail Kubernetes Vulnerability That Enables Windows Node Takeover
Details have been made public about a now-patched high-severity flaw in Kubernetes that could allow a malicious attacker to achieve remote code...
-
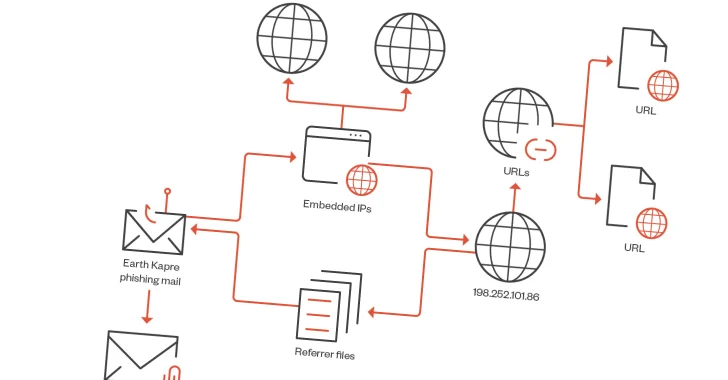
 2.0KMalware
2.0KMalwareRedCurl Cybercrime Group Abuses Windows PCA Tool for Corporate Espionage
The Russian-speaking cybercrime group called RedCurl is leveraging a legitimate Microsoft Windows component called the Program Compatibility Assistant (PCA) to execute malicious...
-

 438Vulnerabilities
438VulnerabilitiesLazarus Hackers Exploited Windows Kernel Flaw as Zero-Day in Recent Attacks
The notorious Lazarus Group actors exploited a recently patched privilege escalation flaw in the Windows Kernel as a zero-day to obtain kernel-level...
-

 4.5KMalware
4.5KMalwareMeta Warns of 8 Spyware Firms Targeting iOS, Android, and Windows Devices
Meta Platforms said it took a series of steps to curtail malicious activity from eight different firms based in Italy, Spain, and...
-

 3.1KVulnerabilities
3.1KVulnerabilitiesMicrosoft Rolls Out Patches for 73 Flaws, Including 2 Windows Zero-Days
Microsoft has released patches to address 73 security flaws spanning its software lineup as part of its Patch Tuesday updates for February...
-

 1.5KMalware
1.5KMalwareNew Mispadu Banking Trojan Exploiting Windows SmartScreen Flaw
The threat actors behind the Mispadu banking Trojan have become the latest to exploit a now-patched Windows SmartScreen security bypass flaw to...
-

 3.3KMalware
3.3KMalwareNew ZLoader Malware Variant Surfaces with 64-bit Windows Compatibility
Threat hunters have identified a new campaign that delivers the ZLoader malware, resurfacing nearly two years after the botnet’s infrastructure was dismantled...
-

 4.6KMalware
4.6KMalwareMalicious PyPI Packages Slip WhiteSnake InfoStealer Malware onto Windows Machines
Cybersecurity researchers have identified malicious packages on the open-source Python Package Index (PyPI) repository that deliver an information stealing malware called WhiteSnake...
-
 3.6KData Security
3.6KData SecurityHow to steal Windows password via Outlook email exploiting vulnerabilities in Windows Performance Analyzer (WPA) and File Explorer
Varonis Threat Labs has uncovered a significant vulnerability in Microsoft Outlook (CVE-2023-35636) that allows attackers to access NTLM v2 hashed passwords. This...
-

 518Vulnerabilities
518Vulnerabilities52% of Serious Vulnerabilities We Find are Related to Windows 10
We analyzed 2,5 million vulnerabilities we discovered in our customer’s assets. This is what we found. Digging into the data The dataset...
-

 797Malware
797MalwareHackers Weaponize Windows Flaw to Deploy Crypto-Siphoning Phemedrone Stealer
Threat actors have been observed leveraging a now-patched security flaw in Microsoft Windows to deploy an open-source information stealer called Phemedrone Stealer....
-

 3.9KIncidents
3.9KIncidentsHow to exploit Windows Defender Antivirus to infect a device with malware
Trend Micro’s recent threat hunting efforts have uncovered active exploitation of CVE-2023-36025, a vulnerability in Microsoft Windows Defender SmartScreen, by a new...
-
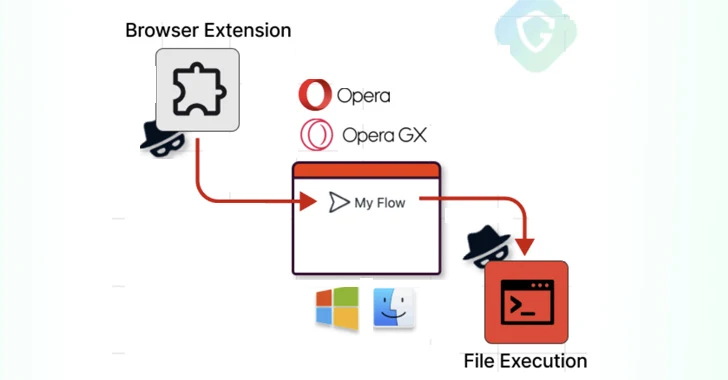
 1.8KVulnerabilities
1.8KVulnerabilitiesOpera MyFlaw Bug Could Let Hackers Run ANY File on Your Mac or Windows
Cybersecurity researchers have disclosed a now-patched security flaw in the Opera web browser for Microsoft Windows and Apple macOS that could be...
-

 2.7KVulnerabilities
2.7KVulnerabilitiesMicrosoft’s January 2024 Windows Update Patches 48 New Vulnerabilities
Microsoft has addressed a total of 48 security flaws spanning its software as part of its Patch Tuesday updates for January 2024....
-

 188Malware
188MalwareNew Bandook RAT Variant Resurfaces, Targeting Windows Machines
A new variant of a remote access trojan called Bandook has been observed being propagated via phishing attacks with an aim to...






