All posts tagged "hacker"
-

 5.0KIncidents
5.0KIncidentsThis politician hacked the iCloud accounts of more than 100 women
A Dutch politician could be living his last days at large, as he is facing a sentence of up to three years...
-

 4.1KData Security
4.1KData SecurityHackerOne platform got hacked by a researcher who reported a vulnerability but never got paid
HackerOne is one of the most important vulnerability reporting platforms, so it has access to large amounts of information, although sometimes that...
-

 393News
393NewsTeenage Hacker’s Parents Sentenced For Transferring His Stolen Cryptocurrency
Elliot Gunton, a UK resident, was first convicted at the age of 16 for breaching the UK telecom giant TalkTalk. He was...
-

 4.7KData Breach
4.7KData BreachThe Biggest and Most Affected Data Breach
There were many data breach 2016. It seemed like there was a new one in the news every other week during that...
-
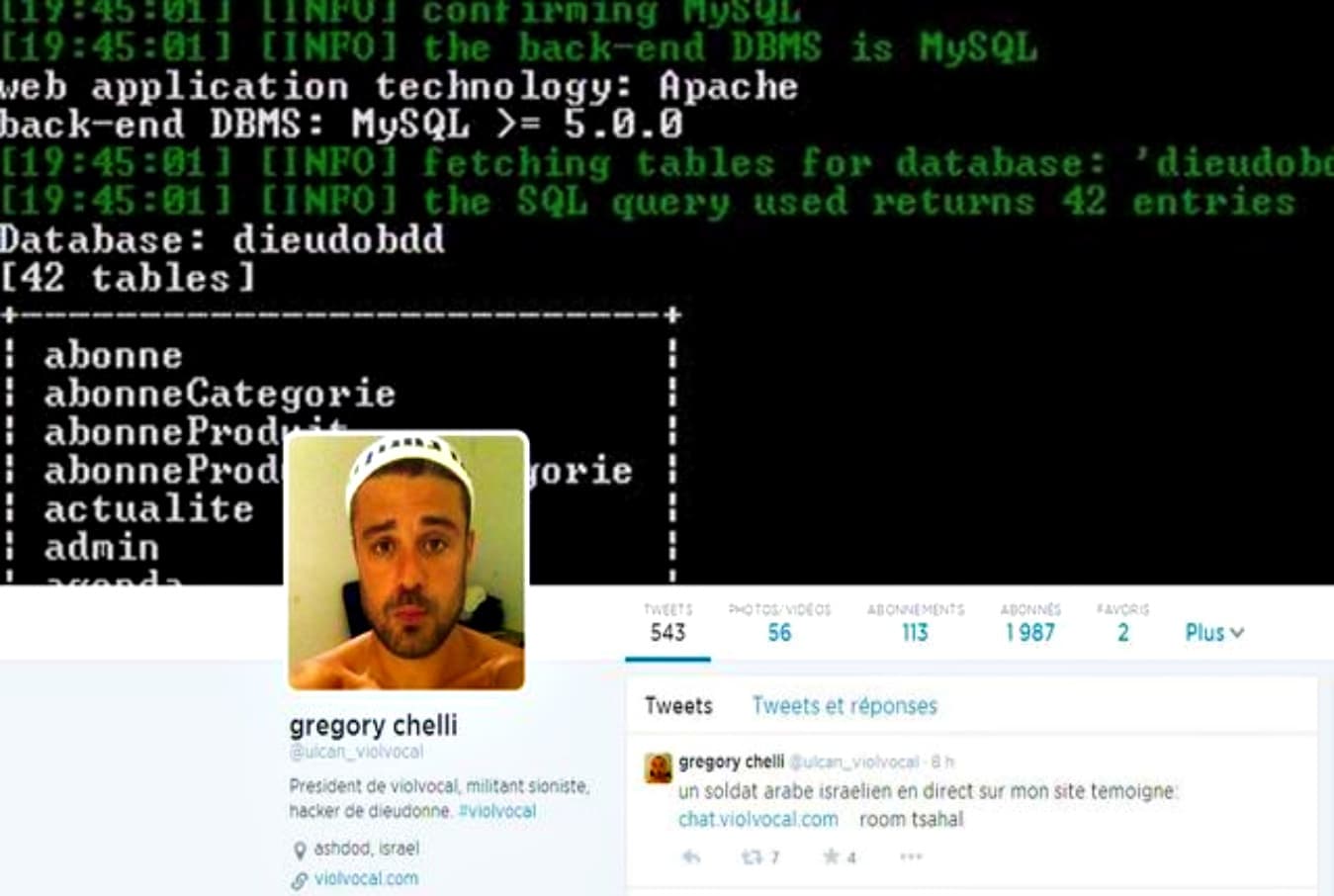
 288Cyber Crime
288Cyber CrimeDeath linked to prank – France seeks extradition of hacker from Israel
The incident took place in 2014 in which father of a French journalist died of a heart attack soon after prank call...
-

 375News
375NewsHackers Hack A Forum For Hacked Accounts: Here’s How
A group of hackers failed to deploy security mechanisms to secure the storage where they store hacked accounts and another hacker group...
-

 451Leaks
451LeaksA Hacker Dumps Over One Billion User Records
According to ZDNet, a hacker by the name Gnosticplayers reveals to them in February about wanting to put up data of over...
-

 252News
252NewsJulian Assange’s Hacking Charges, and Where It Go Wrong
Julian Assange’s lawyers want to see if hacking is protected by the First Amendment. London’s Metropolitan Police arrested Assange on Thursday at...
-

 5.0KCyber Attack
5.0KCyber AttackAustralia’s Election Proposal To Combat Cyber Attack
As a precaution to the risk of getting its election hacked, Australia has to create a special task force that will be...
-

 243Data Security
243Data SecurityUnknown person hacked a judge’s computer to know before anyone a ruling in a trial
Sources close to the best ethical hacking institute and the International Institute of Cyber Security (IICS) have confirmed that Kathryn Schrader, Gwinnett...
-

 319Data Security
319Data SecurityHackers attack manufacturing companies; costumer’s payment information stolen
Criminals have stolen data of Titan Manufacturing and Distributing customers for almost a whole year Malicious hacker groups are attacking manufacturing companies,...
-

 301Incidents
301IncidentsThe Germany politicians’ hacker is just an angry 20 years old man
The suspect claimed to be annoyed by recent statements by some of those involved in leaking information According to reports of cybersecurity...
-

 1.9KCryptocurrency
1.9KCryptocurrencyHacker Compromised JavaScript Library to Steal Bitcoin funds
Event-stream Node.js module called is used in millions of web applications, including BitPay’s open-source bitcoin wallet, Copay. This module was reportedly compromised thanks to the...
-

 307News
307NewsThe Responsible Disclosure of Software Vulnerabilities in the Nutshell
Computer security vulnerabilities are a threat that has spawned a booming industry, between the heightened global focus on security, and the proliferation...
-

 258News
258NewsTesla Model S Stolen, Thieves Hack the Keyless Entry System
A Tesla Model S was stolen recently in Essex, England after a pair of thieves hacked the car’s high-tech keyless entry system....
-
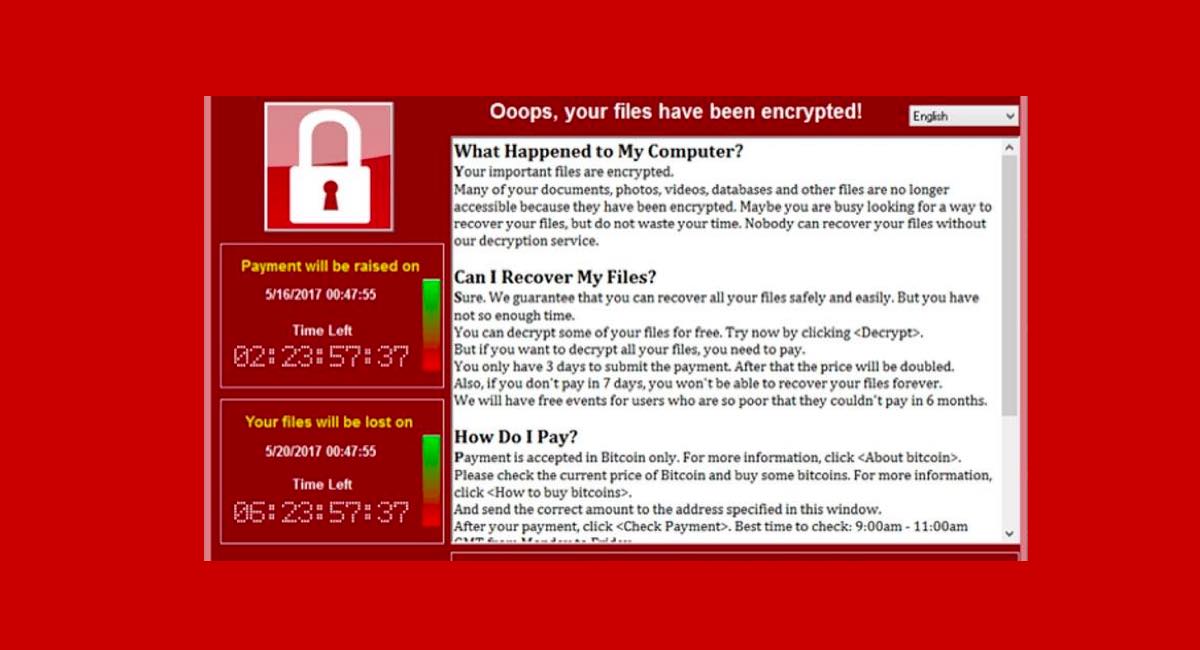
 249Hacked
249HackedNorth Korean Hacker Charged Over WannaCry Attack And Sony Hacking
The U.S. has charged and sanctioned a North Korean hacker who is accused of being responsible for the infamous WannaCry Cyberattacks of...
-

 293Vulnerabilities
293VulnerabilitiesHacker reveals zero-day vulnerability in Windows
The flaw was found in a completely updated system A cyber security organization researcher has publicly disclosed the details about new zero-day vulnerability present...
-

 236News
236NewsHow An Ex-Hacker From The NSA Dominated Def Con Conference
A security researcher has demonstrated, at the recent Def Con security conference, that a Mac computer running Apple’s High Sierra operating system...
-

 204Cyber Crime
204Cyber CrimeIs The World Cup a Hacker’s Paradise?
As the digital world continues to turn, the risk of cyberattack is always on the horizon. And the arrival of the 2018...
-

 227Cyber Crime
227Cyber CrimeThe Surprising Ways Hackers are Exploiting the Cloud
Are hackers smarter and more creative than cyber guardians? This is becoming the eternal question of the digital age. While we would...
-

 297Cyber Crime
297Cyber CrimeThe Different Phases of a Cyber Attack
As we begin to discuss the different phases of a cyber attack, let’s not forget that things are changing drastically as regards...






