All posts tagged "Mac"
-

 2.9KHow To
2.9KHow ToWhat to Do If Your Mac Keeps Freezing
A MacBook is the closest a personal computer gets to perfection. While Windows-based computers are notorious for being laggy and slow, MacBooks...
-

 1.8KNews
1.8KNewsNew Mac Malware Uses ‘Fileless’ Technique To Attack Stealthily
Notorious hacking group Lazarus which is also behind the widespread WannaCry ransomware is trying to infect Mac users with new malware that...
-
 2.1KHow To
2.1KHow ToHow To View Hidden Files On MacOS Using Simple Steps?
It’s not just you, we all want to know why the Mac system takes up so much of space. I am curious...
-

 357Geek
357GeekVulnerability in Zoom video conference app lets Mac’s camera hijacking
The vulnerability in the Zoom video conference app lets attackers hijack Mac’s camera by merely using malicious websites. The Zoom video conference...
-

 497Data Security
497Data SecurityHackers using pirated software to spread new cryptomining Mac malware
If you download pirated content from torrent platforms, you can be a victim of this Mac malware. There is a new variant...
-

 294News
294NewsBird Miner: This Cryptominer Malware Emulates Linux To Attack Macs
One of the biggest disadvantages of using pirated software is the increased risk of letting your computer get infected with malware. Cybercriminals...
-

 282News
282NewsApple’s All New Mac Pro Supports Intel 28 Core Xeon CPU And 1.5TB RAM
After much wait and speculation, Apple has finally launched its most powerful Mac, the Mac Pro. The new ‘cheese grater’ look is...
-

 270Malware
270MalwareAdvanced Retefe Banking Malware Attack on Windows and Mac Users via Weaponized Word Documents
Researchers discovered a new wave of sophisticated banking malware called Retefe that targeting Windows and Mac users financial data by routing the...
-
 278Security Tools
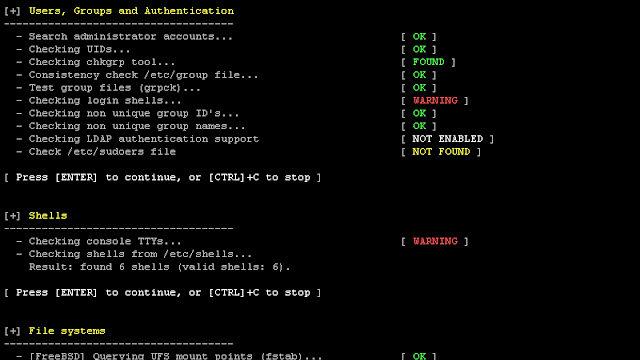
278Security ToolsLynis 2.7.3 – Security Auditing Tool for Unix/Linux Systems
We are excited to announce this major release of auditing tool Lynis. Several big changes have been made to core functions of...
-
 267Exploitation Tools
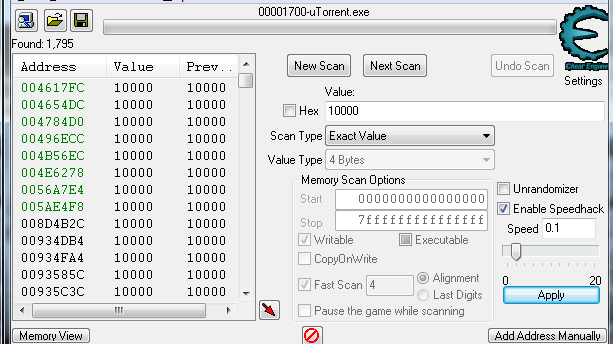
267Exploitation ToolsCheat Engine – A Development Environment Focused On Modding
Cheat Engine is an open source tool designed to help you with modifying single player games running under window so you can...
-

 220News
220NewsApple To Ditch Intel Chips In Mac For Its ARM Chips In 2020: Report
Several reports have indicated that Apple is planning to ditch Intel in favor of its own ARM chips for macs in 2020. According to...
-

 333Data Security
333Data SecurityAn info stealer .exe malware is targeting Mac users around the globe
Cybercriminals have identified a unique method of attacking Mac devices, which involves exploiting executable or .EXE files. Those files that can be...
-

 348Geek
348GeekFlaws in RDP protocols leaving machines prone to remote code execution
Major Security Flaws Identified in RDP Protocols making Machines Prone to Remote Code Execution and Reverse RDP Attacks. Check Point researchers have...
-
 221Network Tools
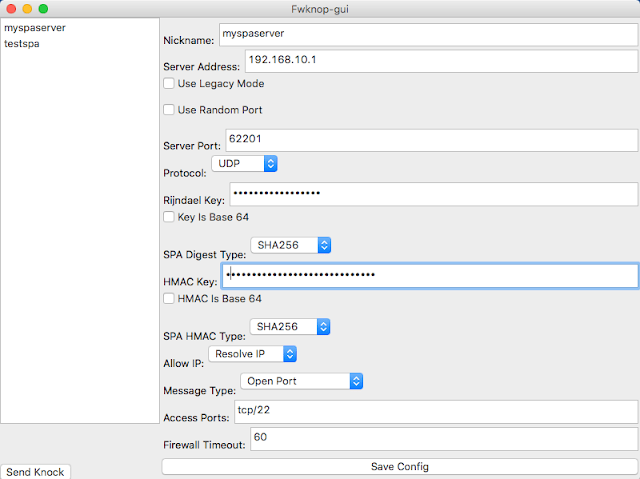
221Network ToolsFwknop – Single Packet Authorization & Port Knocking
fwknop implements an authorization scheme known as Single Packet Authorization (SPA) for strong service concealment. SPA requires only a single packet which...
-

 344Geek
344GeekNew Mac Malware steals iPhone text messages from iTunes backups
The IT security researchers at Palo Alto Networks’ Unit 42 have discovered a dangerous new Mac malware capable of targeting devices for multi-purposes...
-

 354Geek
354GeekAttackers successfully hide Mac malware in ad images
Malware campaigns have become quite regular on Apple devices and as per the new report from Confiant, a cyber-security firm, there’s a...
-

 256Vulnerability Analysis
256Vulnerability AnalysisShodanploit – Shodan Command Line Interface Written In Python
Shodan is a search engine on the internet where you can find interesting things all over the world. For example, we can...
-
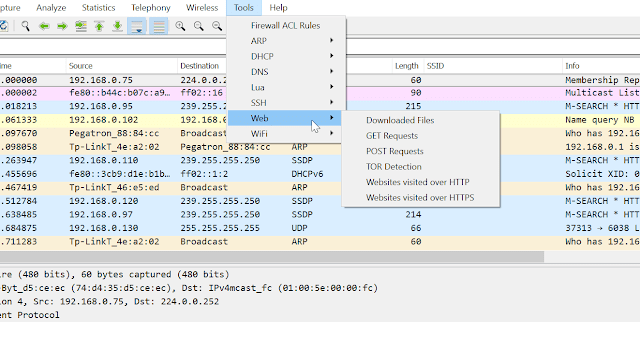
 253Network Tools
253Network ToolsPA Toolkit – A Collection Of Traffic Analysis Plugins Focused On Security
PA Toolkit is a collection of traffic analysis plugins to extend the functionality of Wireshark from a micro-analysis tool and protocol dissector...
-
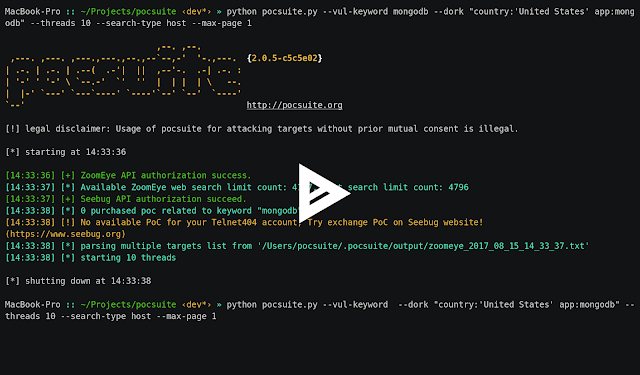
 274Vulnerability Analysis
274Vulnerability AnalysisPocsuite v2.0.8 – Remote Vulnerability Testing Framework Developed By The Knownsec Security Team
Pocsuite is an open-sourced remote vulnerability testing and proof-of-concept development framework developed by the Knownsec Security Team. It comes with a powerful...
-
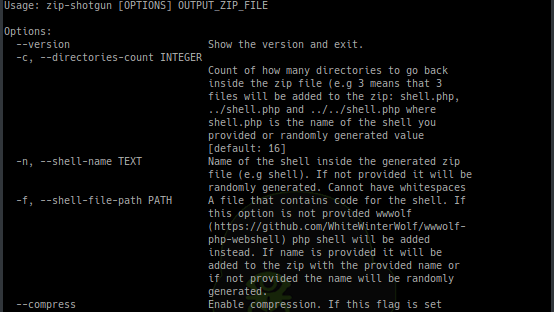
 253Vulnerability Analysis
253Vulnerability AnalysisZIP Shotgun – Utility Script To Test Zip File Upload Functionality For Vulnerabilities
Utility script to test zip file upload functionality (and possible extraction of zip files) for vulnerabilities. Idea for this script comes from...
-
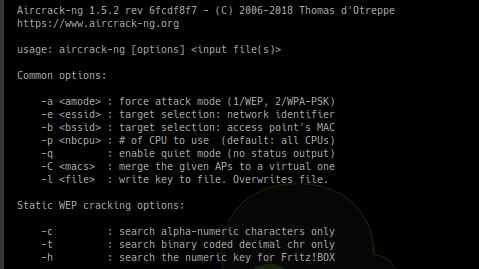
 295Wireless Attacks
295Wireless AttacksAircrack-ng 1.5 – Complete Suite Of Tools To Assess WiFi Network Security
Aircrack-ng is a complete suite of tools to assess WiFi network security. It focuses on different areas of WiFi security: Monitoring: Packet...






